Can you think of life before email? Before telephones? In fact, I wonder what dating was like in the middle ages? Imagine sending a letter to your significant other, perhaps you’d be worried about your delivery person (Leofric – most popular baby names 1384) getting curious and reading your effusive letters? “… And yet much to Leofric’s dismay upon opening thine letter he foundeth nothing but gibberish, this being ok since young Leofric was not able to read anyway.”
You’d probably have used your soaring medieval IQ and created a special letter to number method where a=1 and b=2, etc. and your message was secure even to a delivery person that could read – you’d definitely have been legit back then.
We still want privacy today but being legit is a bit tougher so we use more advanced methods of encryption (think encoding or secret-ing our communication). Blasting our 1’s and 0’s into the air like we do today makes it that much more important since anyone with a little time, equipment and motivation could intercept and read your stuff.
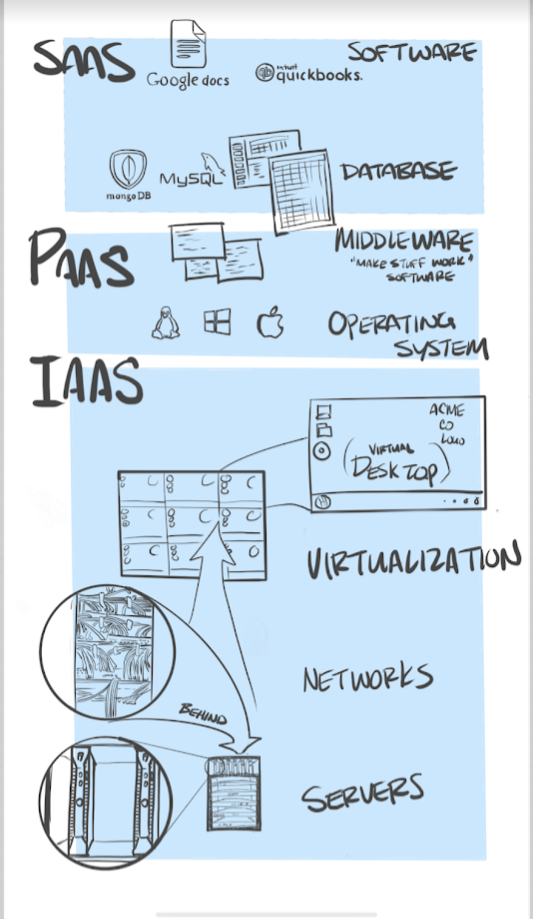
Protocols, Encryption, Algorithms
We call the methods we use today to safely send messages a protocol. We talked about these sets of rules a bit before. Pre-2020 our brains would run a protocol/set of rules when we’d meet someone:
- greet person
- say your name
- find out their name
- shake hands – whoops, had to change that part of the protocol in 2020 didn’t we!
Similarly there are a bunch of protocols that run in the background of the tech we use (don’t worry if they are not familiar – there is a similar thread we are going to connect them on)
- SMTP = recipe to securely transferring email
- SFTP = securely transferring a file
- TLS = recipe to securely transfer data across the internet
Inside each of those rules sets is a key step called encryption, this is the more sophisticated version of what we talked about in the opening when we imagined turning a=1, etc.
Just like we use specific language like protocols and encryption. We call this encryption step an algorithm. (don’t worry it is only those 3 annoying terms to nail down and then you’ll be off to the races with some math, yay!) An algorithm is a lot like a recipe: very specific steps that if you don’t follow you get one of these really marketable “Pinterest fails” (Wow, there is a whole series on it now, welcome to the twenty-weirdth century, rad.)

https://www.businessinsider.com/nailed-it-netflix-baking-fails-photos-2018-3
Alright so quick check: you’ve totally got this down: protocol, encryption, algorithm. Let’s take this on…
RSA
The RSA algorithm is a recipe for encrypting your data, it is used in different protocols listed above (SFTP, SMTP, TLS). It was invented by 3 genius humans named: Rivest–Shamir–Adleman. It is important because understanding this means understanding the core principle modern security is built on.
Ok, but how the hake does this thing work? It goes like this:
You type your email, ponder over it one more time, and click send which wakes up this dude who we will call “robot”1Remember when we talked about software is like a robot brain, bet you didn’t realize how handy that’d be right? This robot would be the portion of software in your email program that runs all of these steps to make your email secure.:
Robot then goes into motion:
“Hey” (looks at the address of the person you are sending to) “You awake?”
This wakes her up, we will call her “robot-ette”. She is the portion of software in your recipient’s email program that runs the steps from the other email account.
robot: “I’ve got a message for you can you tell me your numbers that I need to lock it with?”
robot-ette: “uh, yeah, let me find it….yeah, it is 5,14. Oh by the way I don’t care who ever sees that number so ‘whatevs'”.
robot: “Perfect, let me work on this and I’ll send it right over.”
robot: Ok, my 2-step algorithm says take the first number and do something and then take the result of that and do something else, pretty easy.
1st gotta turn this pondered over email to number.
Oh who am I talking to – I’m a computer, everything is numbers to me, no problem.
[breaking the fourth wall here:] ok, yo, I’m gonna make this more simple and make the logical leap of simplifying the message to a single number: 2 because even hello looks like this: 0110100001100101011011000110110001101111 and to some math is a living hell, so let’s go for simple first..and …back to the story….
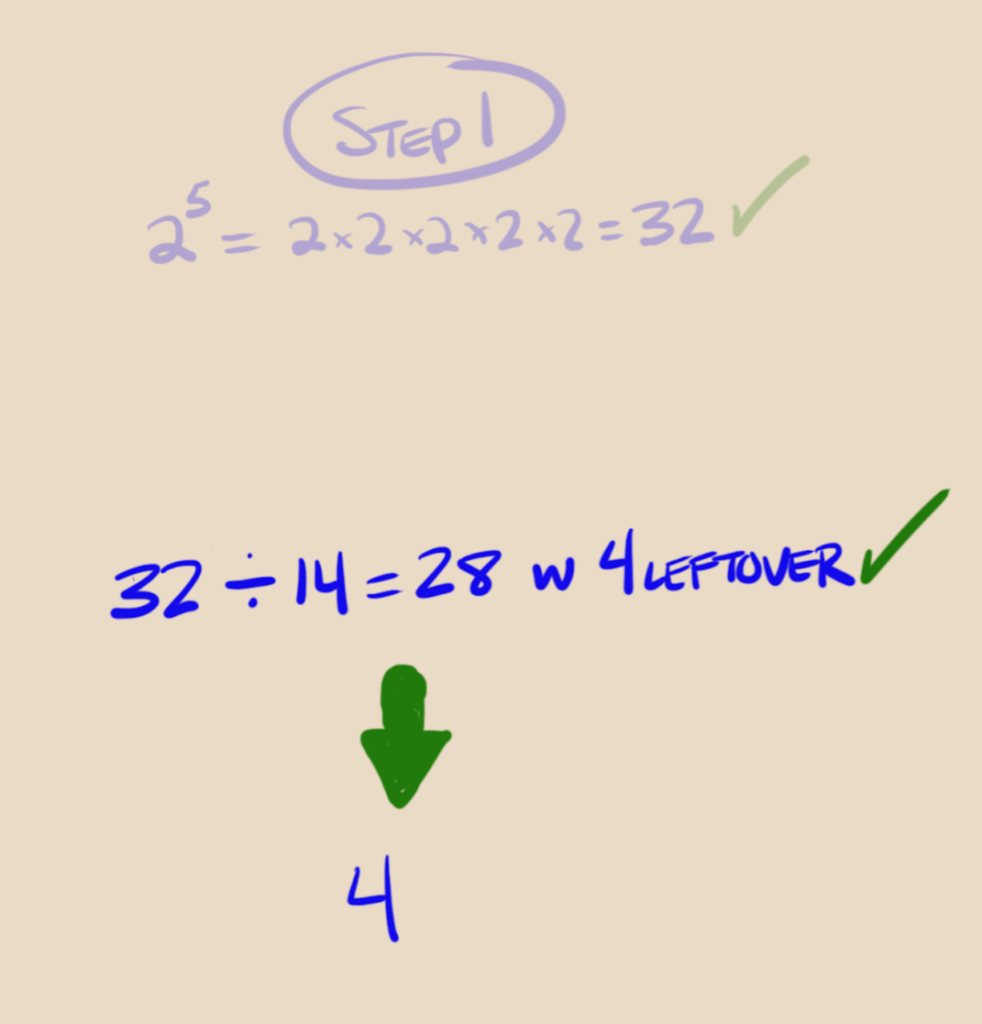
robot’s step 1: ok I’m gonna take the message which is the number 2 and scramble it using robot-ettes numbers 5 and 14. The recipe calls for raising message 2 to the power of her first number 5, same as multiplying 2 by itself 5 times, got it.
ok got it, now step 2: take the results of step 1 which is 32 and divide it by 14 and see what’s left over:
ok, 4! easy!
robot: “Hey, robot-ette, sending now.” “4” races across the internet around the world at the speed of light.
robot-ette: “Ok cool, got the message, gotta run it through my process so my boss can actually read this thing.”
alright two steps for me too:
step 1: I’ve got to run this through my super secret decoder number that no one in the world knows (including the human boss that will read this email – some things are just better not to trust the humans with, eyeroll). Looking left and right, the secret number is 11. (4th wall Mike again: oh yeah, don’t tell anyone…) The algorithm calls for raising 4 to the power of 11, which give me ~4.1 million like below.
step 2: calls for dividing the results of step 1 by 14 and taking what is left over…
robot-ette, oh, ok, the message is 2! I’m sure the boss is really going to like that.
That’s it, that is basically how it works!
In the end, you get your message across safe and secure, nobody hacks it, and life goes on as normal, hey somebody give those robots a treat or something, huh?
Official terms
The number that robot-ette doesn’t care about anyone else seeing? That is called the Public Key. People use your public key to scramble messages to you when they send their message to your email.
When you send messages you lock it using the other person’s public key. (Yes – why in the flyin’ shorts they did not name it a “Public Lock”… I don’t know).
The number that robot-ette doesn’t want anyone to know: that is the Private key and is the key number that unlocks the message.
Together the public and private keys make up Asymmetric Encryption. Sometimes it is easier to learn the process before the labels since you can feel your mind wanting to go to sleep just reading the words “Asymmetric encryption”.
Details, details
Ok earlier I used the phrase “basically how it works”, right? I probably should have used all caps and more exclamation points than will fit on the page cause the principles are right but the real thing is crazier in the following ways.
These prime numbers are sick-freaking gigantic the secret key they produce is 78 digits long. That looks like this: 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936. Ouch, we’ll talk more about it soon.
The math here was really convenient but it can’t just be any prime numbers you have to select numbers using another algorithm so that the trick works.
This core “understanding bridge” I’ve described is surrounded by an industrial-level number of steps that support it and make it work, including something called “Hashing” which happens to be a core step you need to know to pull all of the last 9 articles together and understand the phenomenon called “Bitcoin” or “Cryptocurrency” – which incidentally you can go to by clicking here!